Just ordered one from Amazon. Thanks for the recommendation.
Oh no - it was a joke! I've got that CC2531 on the way, and will make it work one way or another.
But thank you!
Vee
Everyone is eager to have the Xiaomi devices working flawless. 
I can't try it out yet, but my research on a solution for getting packets from the CC2531 sniffer to Wireshark for decryption decoding keeps turning up an open source custom firmware + Windows or Ubuntu client solution called ZBOSS Sniffer. It requires some initial setup in Wireshark, but apparently should do the trick. The only downside is that it seems it hasn't been updated since it was released in 2013.
If you have a Mac, there's also a Python based solution called ccsniffpiper here. The main advantage of this solution is that it works with the original TI firmware for the CC2531, and just creates a pipe that makes the packets available to Wireshark. I plan on trying this solution first when I receive my CC2531. I plan to try this solution if the new TI sniffer software doesn't do the trick.
I found reference to ccsniffpiper in a very informative PDF document explaining how to set up and use Wireshark up to do ZigBee sniffing.
EDIT - I should have just looked at the information on TI's download page for the new version of their SmartRF Packet Sniffer software. It states that the software includes "Dissectors for Wireshark" and that it "uses Wireshark for packet display and filtering". Further down the page, the CC2531 USB Dongle is listed as supported for ZigBee protocol sniffing. So I'll try this solution first!
For those of you that ordered two hubs and have a spare husbzb-1 stick, it looks like you can sniff with that as well.
I just had some success using this library: GitHub - zsmartsystems/com.zsmartsystems.zigbee.sniffer: ZigBee sniffer using Ember NCP and routing packets to Wireshark for display
Theres a compiled jar at the bottom and a pdf to add your network keys (I grabbed the network key using their other zsmartsystems console library and the console command ncpsecuritystate)
java -jar ZigBeeSniffer.jar -port COM14 -baud 57600 -flow hardware -c 14 -w test.pcap
CC2531 from Banggood arrived today, earlier than expected. The link I used to download the SmartRF packet sniffer software didn't include the 64bit Windows 10 Cebal drivers; they are available here: [Resolved] CC debugger driver on windows 10 (64-bit) - Other wireless technologies forum - Other wireless - TI E2E Community
Look for the link to the zip file in the green outlined box on that page; they can be extracted and used to manually install from Windows Device Manager.
I give you full credit for bringing Xiaomi device discussion to top trending subject on this forum! ![]()
![]()
![]()
![]()
![]()
My CC2531 arrived today and I had a quick play
As @guyeeba mentioned above, it doesn't seem to be supported by the TI SmartRF Packet Sniffer 2 software (which outputs to Wireshark) but works with the orginal SmartRF Packet Sniffer software (which is a bit rubbish).
I found this though - Sun May Sky: How to use CC2531EMK and Wireshark as Zigbee sniffer.
And it seems to work ... in as much as I can get data flowing into Wireshark using it.
@guyeeba does this mean your tool isn't needed? Also, do you have any hints on getting the decoding side working with security keys etc?
In case you managed to route the zigbee packets to wireshark, then... no, my tool is for ppl who has to live with the legacy Packet Sniffer (like me).
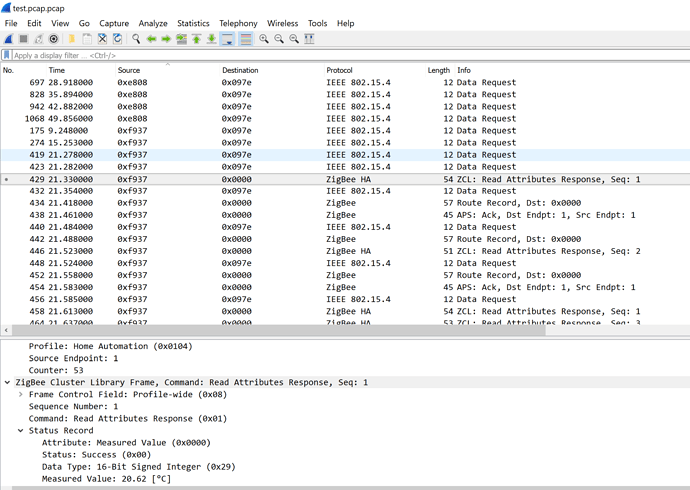
The keys have to be set in Wireshark in Edit/Preferences/Protocols/Zigbee/Pre-Configured Keys dialog (Security level has to be "AES-128 Encryption, 32-bit Integrity Protection".
The first key you need is the Trust Center Key, which is 5A:69:67:42:65:65:41:6C:6C:69:61:6E:63:65:30:39 (Normal byte order).
Then you have to start capturing, and join a new device to the network. In the capture, you'll find a frame where the coordinator sends the network key to the new member of the network (wireshark points to this frame in every decrypted frame's security header in case you don't want to find it manually). You have to add this key to the Pre-Configured Keys list. Wireshark recognizes and uses these keys automatically, but only for the scope of one capture, so it's advised to add all your network keys to the list, so they'll be remembered permanently. 
At the end of the day you'll have a list of keys for all your networks, chosen and used automatically by wireshark, similar to this one:
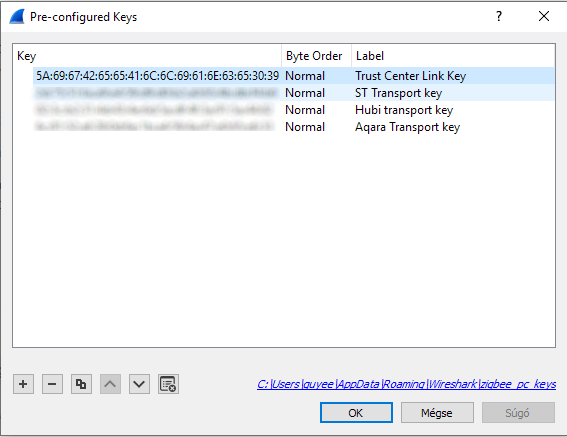
...or at least this is how I remember, but the process is probably quite similar to this one.  But feel free to ask if I forgot something...
But feel free to ask if I forgot something...
Thanks for the pointers, will give that a go later on today ![]()
Yes I was the same ... my CC2531 only worked with the legacy Packet Sniffer ..... but following that link above and it seems to be working with the "TI Wireshark Packet Converter" directly into Wireshark now, so I think it should work for you too?
My CC2531 has no headers to connect it to a CC debugger, so these solutions are not working for me...
...but I had nothing to lose, so I tried it with the stick's original firmware...
...and it's working flawlessly. 
It seems I've always had the sniffer firmware installed. But back in my time this packet converter was probably hidden from google, that's why I decided to make one for myself.
Thanks for convincing me to give it a try! 
Great to hear. I'm hoping all y'all "smarter than me" folks will find it valuable and help us gain better zigbee stability.
No problem, glad it's working for you!
I got my network key earlier today and now just need to get some time with the protocol to understand it more.
One thing I did ask the Wireshark guys was whether they could extend their MAC address lookup via the ethers file to work with 64-bit MAC addresses, as that would allow you to provide a map file to resolve the MAC address to real device names, which would be really useful.
Just an update on the CC2531 board I ordered via Banggood.
I finally had a chance to plug it in a few days ago, and discovered it's a non-working / faulty unit.
Unfortunately, this situation is the one downside to ordering cheap electronic items that are shipped directly in an "ePack" from China: I probably won't ever see either a replacement or my $10 returned. I have had one good experience in past, so I've contacted Banggood to ask for a replacement to be sent. I'm not holding my breath for a response...
In the meanwhile, since I'm getting nowhere with my "project" of getting the sending of the sensitivity level change command to work with the Aqara Vibration sensor, I am going to try converting one of my "extra" Xiaomi Temp-Humidity sensors into a sniffer using these instructions:
If that doesn't work, I have found there's an interesting multi-protocol SoC: the nRF52840, which is found in a couple of USB development dongles from MakerDiary (available for $20 on Amazon US) and Nordic Semiconductor (around $10 from DigiKey or other resellers).
Both USB dongles support Bluetooth LE, Thread, ZigBee, 802.15.4, ANT and 2.4 GHz.
For the Nordic SC dongle, there's already a GitHub repository with an experimental project that includes 802.15.4 sniffer firmware and python-based serial output script to create a port that Wireshark can use. Instructions are provided for configuring Zigbee data capture.
However, for the MakerDiary dongle I only found a wiki article on building a Thread Network sniffer, though it may be possible to adapt it to sniffing ZigBee data, as they're both IEEE 802.15.4 traffic.
Between those two nRF52840-based options, the Nordic SC looks like a best bet, though. I just wish it was on Amazon for $10!
Keith, that really stinks. Mine didn't work until I loaded the TI software.
Are you getting the solid green light when plugged in? And I always use PayPal as whenever there is a problem, and banggood sees PayPal, they make good or else a PayPal claim gets them going.
I can certainly donate mine too a good cause, if you'd like.
God knows if I'll ever be able to wrap my head around the alphabet soup that is those zigbee messages.
Let me know
Unfortunately not.
I did use PayPal, so hopefully I get a positive response. I've never had to make a PayPal claim, but on principle I will if needed.
Don't worry about donating yours, however, because...
I just ordered a Nordic nRF52840 Dongle from Arrow, and it only cost $8.68 (w/12% off first time coupon] with free FedEx overnight shipping.
I have no idea how Arrow can't lose money on offering free overnight shipping with no minimum order, but that was a no-brainer for me.
I guess I will try the nRF52840 before I start hacking and soldering a sniffer out of a Xiaomi sensor!
Were you able to get the 64 bit Cebal drivers to load? I had no luck until I used the drivers here:
https://e2e.ti.com/support/wireless-connectivity/other-wireless/f/667/t/675493?tisearch=e2e-sitesearch&keymatch=cebal%20driver
Rxich, came across this when trying to make wireshark zigbee sniffer with cc2531. I have cc2531 running with TI packet-sniffer V1 (as post #1), but not able to make it work with wireshark. I have window 10. The ZBoss did not show the USB dongle as an option; For TI, wireshark can not connect the pipe device. Not sure if I missed something here.
Will you able to have cc2531 work with wireshark ?
So I think @guyeeba came up with a fix
I also use a CC2531. The only free and compatible software I found was TI's own Packet Sniffer application (the legacy version, not the newer PacketSniffer 2), but that is more or less unusable (does not decrypt messages, and UI is a mess). But it can broadcast the messages to network!
So I wrote an application that receives these messages, transforms them from TI's format to a Wireshark-supported protocol (ZEP), and sends these packets to localhost - so that I can easily capture them in Wireshark.
With this setup I only had to buy a CC2531 stick, and now I can sniff my network keys, store them in Wireshark, and all my Zigbee PANs are decrypted automatically... extremely convenient!
But it could be even more convenient if I could eliminate both Packet Sniffer and my tool, so in case anyone finds a way to integrate a cheap aliexpress CC2531 to wireshark