I'm having this issue as well. It always seems to happen overnight but I can't verify that the time has anything to do with it. It's probably happening once every couple of weeks.
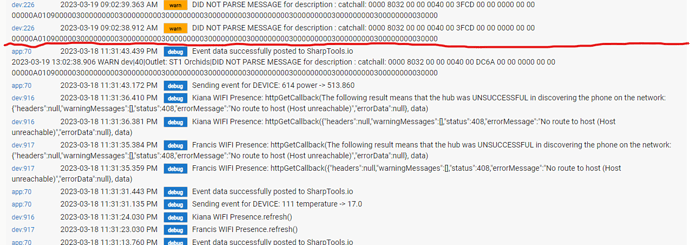
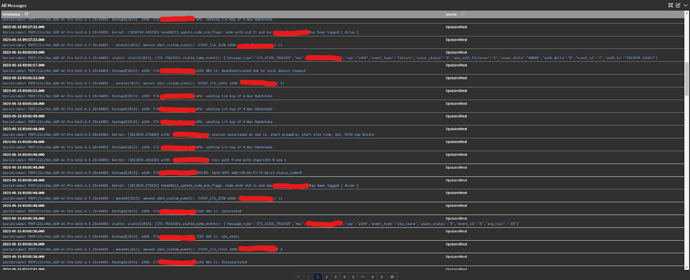
In the below logs, you can see that it disassociates at 3:01:36 and then attempts to re-associate, but apparently the handshake never completes and the AP drops (deauths) the client.
You can then see at 9:57 when I power cycled the hub.
There's nothing in the hub logs around that time.
In addition to the device being disconnected from the wifi, it seemed to be otherwise unresponsive - I have a Z-wave scene controller that I attempted to use and it did not work.
Obviously I wasn't able to get to the web interface or the thing on 8081 since it was off the network.
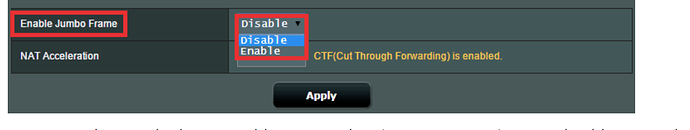
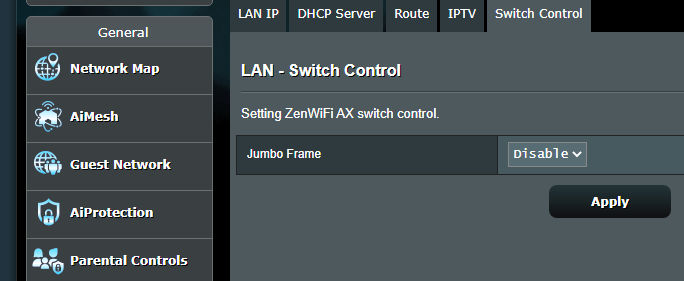
I do have jumbo frames enabled on my network, but that will require a lot of reconfiguration of other devices if I disable it, so that's not going to happen. I do not have problems with any other devices due to jumbo frames and I don't have any other devices with wifi connectivity issues.
The hub is probably 10 feet from the access point it's using so range isn't an issue.
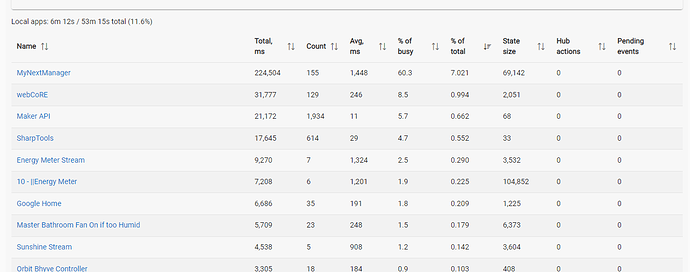
I am currently running 2.3.5.135, I do see there is a fix related to wifi in 2.3.5.138 so I'll update it. I don't log into the hub very often, so every time I have encountered this issue, it turns out I'm a version or two behind 
I've redacted the mac addresses. I pasted a screen shot of the logs below as well as a copy of that data in CSV format.
timestamp,source,message
2023-05-15T03:01:36.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ IEEE 802.11: disassociated"
2023-05-15T03:01:36.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ IEEE 802.11: sta_stats"
2023-05-15T03:01:36.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: : wevent[2012]: wevent.ubnt_custom_event(): EVENT_STA_LEAVE ath0: @@MAC@@ / 4"
2023-05-15T03:01:38.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""sta_leave"",""assoc_status"":""0"",""event_id"":""6"",""avg_rssi"":""-65""}"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/4 msg of 4-Way Handshake"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: : wevent[2012]: wevent.ubnt_custom_event(): EVENT_STA_JOIN ath0: @@MAC@@ / 11"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1813850.279889] ath0: [@@MAC@@] station associated at aid 11: short preamble, short slot time, QoS, HT20 cap 0x1431"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1813850.279828] ieee80211_update_node_ecm_flags: node with aid 11 and mac @@MAC@@ has been tagged [ dvlan ]"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ IEEE 802.11: associated"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA f0:9f:c2:2d:c9:ec DRIVER: Send AUTH addr=@@MAC@@ status_code=0"
2023-05-15T03:01:48.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1813850.201838] ath0: [@@MAC@@] recv auth frame with algorithm 0 seq 1"
2023-05-15T03:01:49.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/4 msg of 4-Way Handshake"
2023-05-15T03:01:50.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/4 msg of 4-Way Handshake"
2023-05-15T03:01:51.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/4 msg of 4-Way Handshake"
2023-05-15T03:01:52.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: : wevent[2012]: wevent.ubnt_custom_event(): EVENT_STA_LEAVE ath0: @@MAC@@ / 11"
2023-05-15T03:01:57.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ IEEE 802.11: deauthenticated due to local deauth request"
2023-05-15T03:02:03.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""failure"",""assoc_status"":""0"",""wpa_auth_failures"":""1"",""assoc_delta"":""80000"",""auth_delta"":""0"",""event_id"":""7"",""auth_ts"":""1813850.216412""}"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/4 msg of 4-Way Handshake"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: : wevent[2012]: wevent.ubnt_custom_event(): EVENT_STA_JOIN ath0: @@MAC@@ / 11"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1838794.449362] ath0: [@@MAC@@] station associated at aid 11: short preamble, short slot time, QoS, HT20 cap 0x1431"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1838794.449298] ieee80211_update_node_ecm_flags: node with aid 11 and mac @@MAC@@ has been tagged [ dvlan ]"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ IEEE 802.11: associated"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1838794.377570] ath0: [@@MAC@@] recv auth frame with algorithm 0 seq 1"
2023-05-15T09:57:32.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA f0:9f:c2:2d:c9:ec DRIVER: Send AUTH addr=@@MAC@@ status_code=0"
2023-05-15T09:57:33.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: pairwise key handshake completed (RSN)"
2023-05-15T09:57:33.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: received EAPOL-Key frame (4/4 Pairwise)"
2023-05-15T09:57:33.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 3/4 msg of 4-Way Handshake"
2023-05-15T09:57:33.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: received EAPOL-Key frame (2/4 Pairwise)"
2023-05-15T09:57:34.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: : wevent[2012]: wevent.ubnt_custom_event(): EVENT_STA_IP ath0: @@MAC@@ / 10.1.3.217"
2023-05-15T09:57:34.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1838796.393797] [DHCP-SM] @@MAC@@: r-40-a"
2023-05-15T09:57:43.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ RADIUS: starting accounting session 6CF1FB61FB24BFBC"
2023-05-15T09:57:47.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""soft failure"",""assoc_status"":""0"",""ip_delta"":""2020000"",""ip_assign_type"":""dhcp"",""wpa_auth_delta"":""970000"",""assoc_delta"":""70000"",""auth_delta"":""0"",""event_id"":""1"",""auth_ts"":""1838794.392898"",""avg_rssi"":""-62""}"
2023-05-15T09:58:14.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""traffic_delta"":""41770000"",""dns_responses"":""2"",""ip_delta"":""2020000"",""ip_assign_type"":""N/A"",""wpa_auth_delta"":""970000"",""assoc_delta"":""70000"",""auth_delta"":""0"",""event_id"":""1"",""dns_resp_seen"":""yes"",""avg_rssi"":""-63""}"
2023-05-15T09:58:34.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-64""}"
2023-05-15T09:59:14.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-66""}"
2023-05-15T09:59:37.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-68""}"
2023-05-15T10:00:07.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-65""}"
2023-05-15T10:01:37.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/2 msg of Group Key Handshake"
2023-05-15T10:01:38.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: group key handshake completed (RSN)"
2023-05-15T10:01:38.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: received EAPOL-Key frame (2/2 Group)"
2023-05-15T10:05:04.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1839246.454386] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a"
2023-05-15T10:38:25.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-64""}"
2023-05-15T10:39:39.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1841320.718799] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a-406000-r-30-a-419030-r-20-a-411010-r-90-a-421040-r-30-a-417010-r-20-a"
2023-05-15T10:46:31.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1841732.757659] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a-406000-r-30-a-419030-r-20-a-411010-r-90-a-421040-r-30-a-417010-r-20-a-412010-r-30-a"
2023-05-15T10:53:07.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1842128.785585] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a-406000-r-30-a-419030-r-20-a-411010-r-90-a-421040-r-30-a-417010-r-20-a-412010-r-30-a-396010-r-20-a"
2023-05-15T10:55:39.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: stahtd: stahtd[2013]: [STA-TRACKER].stahtd_dump_event(): {""message_type"":""STA_ASSOC_TRACKER"",""mac"":""@@MAC@@"",""vap"":""ath0"",""event_type"":""fixup"",""assoc_status"":""0"",""event_id"":""1"",""arp_reply_gw_seen"":""yes"",""dns_resp_seen"":""yes"",""avg_rssi"":""-65""}"
2023-05-15T11:00:08.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1842549.824767] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a-406000-r-30-a-419030-r-20-a-411010-r-90-a-421040-r-30-a-417010-r-20-a-412010-r-30-a-396010-r-20-a-421020-r-30-a"
2023-05-15T11:01:38.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/2 msg of Group Key Handshake"
2023-05-15T11:01:39.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: group key handshake completed (RSN)"
2023-05-15T11:01:39.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: received EAPOL-Key frame (2/2 Group)"
2023-05-15T11:01:39.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: hostapd[2015]: ath0: STA @@MAC@@ WPA: sending 1/2 msg of Group Key Handshake"
2023-05-15T11:07:06.000-04:00,UpstairsWest,"UpstairsWest f09fc22cc9ec,UAP-AC-Pro-Gen2-6.5.28+14491: kernel: [1842967.864298] [DHCP-SM] @@MAC@@: r-40-a-450030-r-30-a-406000-r-30-a-419030-r-20-a-411010-r-90-a-421040-r-30-a-417010-r-20-a-412010-r-30-a-396010-r-20-a-421020-r-30-a-418000-r-40-a"