This makes sense to me in terms of how to view what the VPN is doing :-)![]()
Yes this can be done with an ASUS router OpenVPN server. In a generic openvpn configuration file, I believe this would be “push”ing the LAN to clients, I can’t quite remember what the setting is called in the ASUS GUI but it must be something similar.
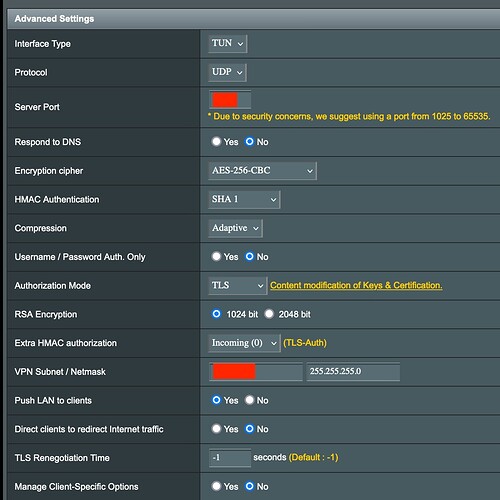
Edit: just VPN’ed into my LAN using the openvpn app on my iPhone, so i could check the router config page. “Push LAN to clients” is indeed what it’s called. I freaking love the remote access options I have with my ASUS router ![]() .
.
I am also running OpenVPN on an old RT-AC66R ASUS router but cannot get it working with my hub. It's connecting in the browser but not sending back any data. Chrome says:
This page isn’t working
192.168.1.125 didn’t send any data.
ERR_EMPTY_RESPONSE
The router UI works fine over VPN, as does an old NAS I have. I set that up many years ago so I don't remember if I had to do any special configuration for that.
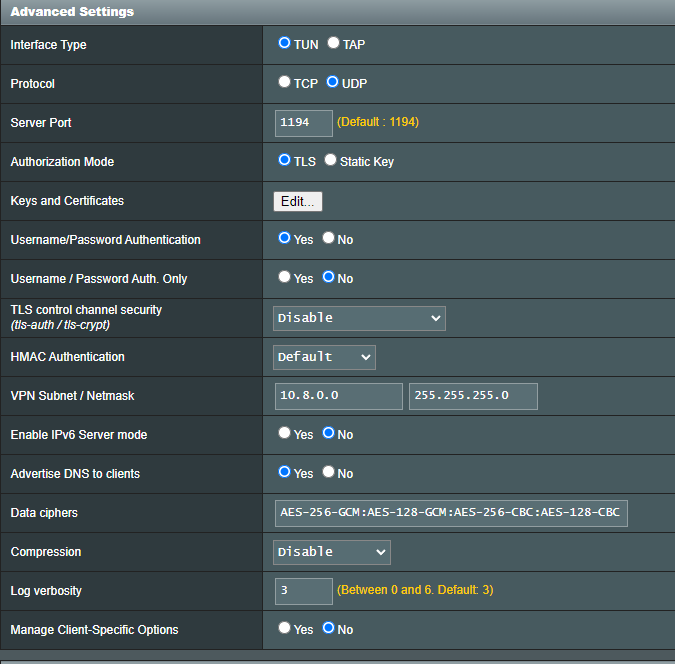
When you switch to Basic settings, there is an option to access LAN, Internet or Both. I have mine set to Both. Here are the rest of my settings on a newer model. I think with my older AC56U I had a custom setting below that would push the 192.168.1.x network to the VPN clients. I will see if I can find it.
UPDATE: The setting I used on my old Asus router was this push route, in the "Custom Configuration" at the bottom. You can force a route to a specific IP this way (your hub). Here is an old post I found about it, I am sure you can find more info in OpenVPN docs or something.
https://forums.openvpn.net/viewtopic.php?t=9055
So maybe (give your hub a fixed IP assignment on the router side)
push "route 192.168.1.125 255.255.255.0"
No dice. I switched to Both. I also disabled compression which I noticed you had. Is there something I need to add in the client config for the push route? Can you share your ovpn file (minus certs and hostnames of course).
If you can SSH to your router, run: cat /etc/openvpn/server1/config.ovpn
For me there is a push route in there already which reads:
push "route 192.168.1.0 255.255.255.0 vpn_gateway 500"
This is supposed to push a route to the clients that anything for 192.168.1.x should connect to the vpn_gateway which will get translated to your router IP when the config loads.
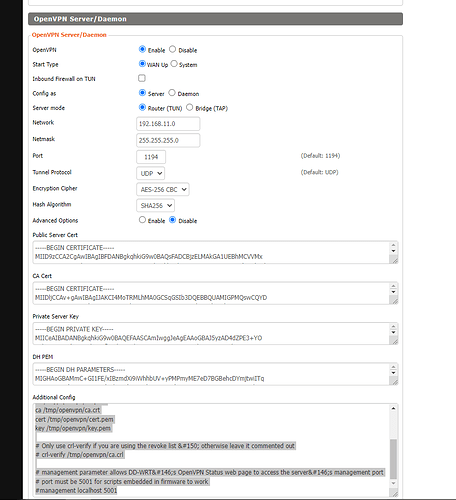
I remember having to add something like this to my old router, not sure if the OpenVPN implementation was broken or what. Do you have a "Custom Configs" section at the bottom of the page like this:
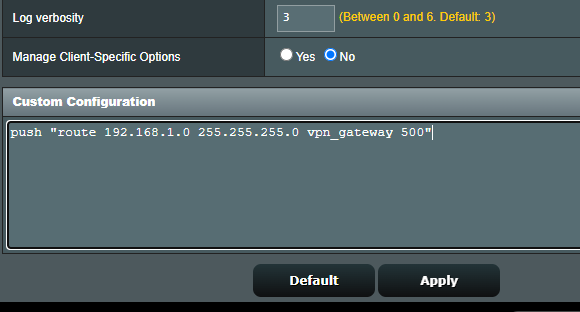
That is where the route would go (I just pasted it into mine for an example)
Here is an old thread about it on the Asus-Merlin forums with another way of setting up using the client config. The user on that thread [Martineau] is very knowledgeable.
this is my open vpn config file i use on my dd-wrt routers.. i can then access my hubitat fine behind it..
note my subnet is 192.168.11.x not 1.x
push "route 192.168.11.0 255.255.255.0"
server 10.9.0.0 255.255.255.0
dev tun0
proto udp4
keepalive 10 120
dh /tmp/openvpn/dh.pem
ca /tmp/openvpn/ca.crt
cert /tmp/openvpn/cert.pem
key /tmp/openvpn/key.pem
Does your router have Asus's InstantGuard (i have an RT-AX3000 that has it baked in) I have found that to be a much easier, much more reliable option than using OpenVPN. Supposedly wire guard is also supposed to be baked in, but ill be darned if I can find those settings.
Are you asking me or someone else?
Some versions of ddwrt have wireguard. Mine does not. I have only pptp and openvpn server support.
I also have used ssh to keep a reverse tunnel up to the router so i can get access behind the carrier nat crap.
I wish I could use wireguard based on what I have read on these forums, but my firmware does not support it (and I doubt it will ever). It sounds like InstantGuard is a newer technology also, which mine does not have.
@jtp10181 my config.ovpn already has push "route 192.168.1.0 255.255.255.0 vpn_gateway 500" plus the one for my hub IP that you had me add.
@kahn-hubitat is that your entire config.ovpn? Mine has tons of more settings. Maybe I need to simplify.
# Automatically generated configuration
# Tunnel options
proto udp4
multihome
port 37394
dev tun21
sndbuf 0
rcvbuf 0
keepalive 10 30
up '/etc/openvpn/ovpn-up'
down '/etc/openvpn/ovpn-down'
setenv ovpn_type 0
setenv unit 1
script-security 2
daemon vpnserver1
verb 3
status-version 2
status status 10
plugin /usr/lib/openvpn-plugin-auth-pam.so openvpn
# Server Mode
server 9.7.0.0 255.255.255.0
duplicate-cn
push "route 192.168.1.0 255.255.255.0 vpn_gateway 500"
push "redirect-gateway def1"
push "dhcp-option DNS 192.168.1.1"
# Data Channel Encryption Options
auth SHA1
cipher AES-256-CBC
# TLS Mode Options
ca ca.crt
dh dh.pem
cert server.crt
key server.key
tls-auth static.key 0
# Custom Configuration
push "route 192.168.1.116 255.255.255.0"
Yes that's my entire config on server side . Do u need to see clients config?
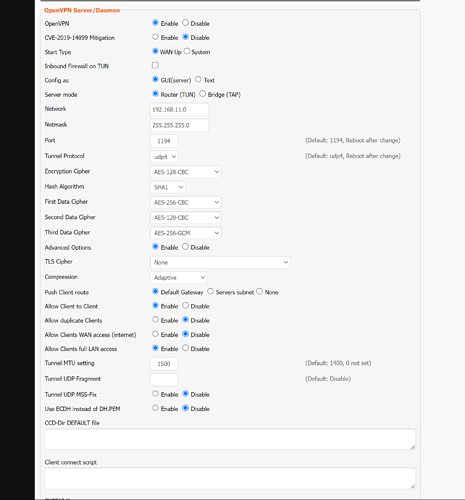
if you have a newer version of dd-wrt . which i just set up.. turn off the cve2019 radio button otherwise routing was not working
ie
What firmware are you running? Asus stock or Asus-Merlin, or the Merlin LTS fork from John?
Ddwrt
Sorry for the delayed response. I was away from this location and didn't want to screw up the VPN config that would cut it off completely.
Anyway, I started from scratch trying to use the default settings and what @jtp10181 shared in his screen shot. It's working!
Here are the differences in the config files. On the server side, these options are now removed:
push "redirect-gateway def1"
push "dhcp-option DNS 192.168.1.1"
tls-auth static.key 0
On the client side, I now see these entries:
sndbuf 0
rcvbuf 0
auth SHA1
remote-cert-tls server (the old config has ns-cert-type server)
and the following are removed from the client config:
key-direction 1
resolv-retry infinite
<tls-auth> key
Thanks so much for the help with this. I really appreciate everyone's time.