I've been considering getting a Firewalla to provide a whole home VPN for my house as well as providing VPN on our devices when we're on the go and dropping my subscription with ipvanish. There is a VPN server built in to Firewalla, do you think I would be able to access my Hubitat hub as if I was on my home network through it?
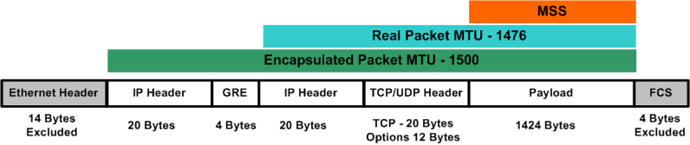
I don't see why it wouldn't .. Only issue might be MTU related
Cool... What's MTU?
I own a Firewalla and I am happily using the VPN to connect to my vacation home to manage my Hubitat. I actually own 2 Firewallas and I am going to connect them via VPN to have a seamless connection.
Highly recommend them as nice firewalls.
Maximum Transmit Unit
It is the maximum packet size you can send .. When you tunnel through a vpn the MTU is smaller and some (poorly configured) ssl connections will fail.. If PMTUD (Path MTU Discovery) is not enabled or overly paranoid firewalls drop ICMP packets then the packets will be dropped that are larger than MTU that your interface can support..
Some people stubbornly assume every packet can traverse the internet intact at 1500 bytes ..
Running a VPN to tap into your network, and connecting to a VPN to mask your internet traffic are two separate uses of a VPN. You might want to consider why you are using ipvanish and if you still want those features. Adding a VPN to access HE is great, but not a good reason to ditch ipvanish if you want the privacy for your web traffic. From what I see Firewalla (or most any other firewall) will not mask your IP traffic like ipvansih, if that is something you want to keep.
I run Untangled on a old Dell box. I like it because (#1 it is free) I am not bound to one piece of hardware. Older PCs (for me) are dime a dozen, so I can slap it on anything as long as it has two NICs.
If you do get Firewalla make sure you get the blue one. 100Mb internet will join dial up soon!
@Kulfsson, you're using a Firewalla, would you say it masks your traffic whether you are on your home network or away from it? Maybe I'm understanding it wrong.
I know you responded to @Kulfsson, so I will let him speak to the Firewalla capabilities (he will know far better than I)
To make sure we understand the many uses of VPN I will give a quick 2 cent explanation. I hope it helps.
VPN's had a renewed life when Internet Service Providers were allowed to start tracknig your outbound web traffic and selling that data. IPVanish and others have created VPN servers around the world for users to log into and "hide" that traffic. Once connected to their VPN, all outbound traffic will not be "seen" by your ISP (since your outbound traffic goes to the VPN server first, then out to the internet).
A VPN- Virtual Private Network, has two parts, a server and client. The server is set up at location A. When you are at location X, Y, or Z. You can "tunnel" back into your network using the VPN connection. Once connected you are "virtually" at the server location A. All your internet traffic goes out via the connection at location A instead of location X, Y, or Z. The ISP at location A can see the traffic going out.
With a home based VPN your house (Firewalla) is the server. When your phone or laptop (the client) are at Starbucks the VPN mask your data, so no one at Starbucks, or the Starbucks ISP can "see" your traffic, but your ISP at home "sees" all the traffic you are sending out (tracking and selling it).
With IPVanish, you connect to their server in Katmando. Only the ISP in Katmando "sees" the traffic, but the ISP in Katmando does not know it is "your" traffic. In that setup they cannot sell "your" data because they do not know who/where "you" are located only the IPVanish server.
I personally do not care that Verizon sell all my data, and do not use a VPN for that reason. There are people on both sides of that discussion, and I am not saying either is right or wrong. With either opinion the technology does not change.
Also know you can have a VPN for internal traffic and still use IPVanish for masking outbound traffic. I just wanted to make sure you understood that difference use cases of each VPN, and decide which is best for your situation.
No, it does not mask my browsing, but you can do that by having a subscription for a VPN service and connect that to the Firewalla and the choose the devices you want to mask. The VPN I use is a built in client VPN service that allowsme to connect to the vacation home while out and about.
That looks like a nice little device, but are you interested in the other features it offers?
If your primary goal is a VPN to allow for remote access to your LAN, then it’s pretty straightforward to setup an OpenVPN server at home, which is free.
Technically I think you could do all the things that box does for free, but of course the time/effort/complexity involved would go up as you roll out additional services yourself.
Thanks for that detailed answer.
So all I'm really looking for is something that would run my whole house through a VPN, mainly for security, but also provide security when using public wifi.
Are there any plug and play boxes, similar to Firewalla, out there that do that? I don't want to have to piece together something on an old computer or a raspberry pie. And trying to avoid monthly subscription costs for eternity.
Edit: @marktheknife oops I posted my response and then saw your new post. I think my new post clarifies what I'm trying to do?
I feel like you might still not be 100% there in terms of what VPNs do.
A VPN server in your home is for remotely connecting to your home from a device when you’re away. It provides encryption for the connection and allows your device to be treated as though it were physically on the LAN. In that sense, it secures the remote connection you are making into your own home.
It doesn’t offer any kind of security when you are at home and using the internet from your devices inside your home.
I also think we need to divide "security" and "privacy".
There ware two types of basic traffic on the internet. You going out to it (surfing the web, Alexa) , and it coming in to you (downloads, streaming, intrusion attempts).
Firewalls "secure" inbound traffic to prevent unwanted people getting in. This does nothing for the privacy of your outbound traffic.
If you want to go out to the internet without being tracked "privacy" use a RELIABLE VPN provider. (IPVanish is good, others sell your traffic so whats the point?)
So which is it security or privacy?  Both requires both.
Both requires both.
Ok so Firewalla is basically a firewall but with a built in vpn server that I can access remotely thus securing my data back to the house but then it's not secure from there out. I thought somehow it was securing my data from my whole home somehow.
So to do everything I want, I need a VPN server of some type at home to access Hubitat remotely but then would i have to look at something like custom firmware router that I can connect directly to someone like IPVanish to put my whole home on a VPN? I was hoping this wasn't the case as I would like to ditch the monthly cost and I use Google wifi and have some money invested in that hardware that I don't want to abandon yet.
I looked around the house and I have an old Netgear wndr3700 wireless router. It looks like I can Flash a version of dd-wrt firmware on to this, connect to ipvanish, then put the router in bridge mode and connect it inbetween my modem and Google wifi to put my whole home on VPN? That would take care of the whole home VPN part I guess?
Accessing Hubitat remotely can wait I guess, no biggie.
If you want to access hubitat remotely, you would need a VPN server running inside your home.
A service like IP vanish needs a server running somewhere else, all the traffic that originates in your house going to that server first does not provide security, per se, as @TechMedX aptly points out. It makes it so that someone like your ISP has no idea which website you were visiting. If you live in a country where you could be imprisoned or killed for visiting certain sites, then being protected from that would also be good from a security perspective.
A VPN server that someone else runs as a commercial service will charge you for that service.
Possibly? I’m far from an expert at this stuff. But I still managed to setup an OpenVPN server at home ![]() .
.
You would need to set your google wifi router to port forward incoming VPN connections to the flashed Netgear router running dd-wrt with the VPN server. That much I know at least.
I don't think the router will run a VPN server, it will just direct all of my home's outgoing traffic through ipvanish if I tell it to, as far as I understand. I now see that I would also have to run a VPN server to access my Hubitat remotely and in that case I would probably have to port forward as you mentioned.
If you're talking about a router that runs dd-wrt, then I want to clarify that dd-wrt can definitely run OpenVPNd. I used dd-wrt for 3-4 years and used it to VPN into my home network.
Also want to point out that Firewalla doesn't play nice with some mesh networks. For example, I know Google WiFi is not very popular, but it is more than adequate for the network tier I pay Cox for (100Mbps). Firewalla Red wouldn't work with it. I took it out and replaced with a Fingbox that has worked perfectly.
Edit: Fingbox also works by ARP spoofing. Firewalla wouldn't work if I let Google WiFi handle DHCP requests. And if I configured Firewalla to handle DHCP, the network would slow to a crawl.