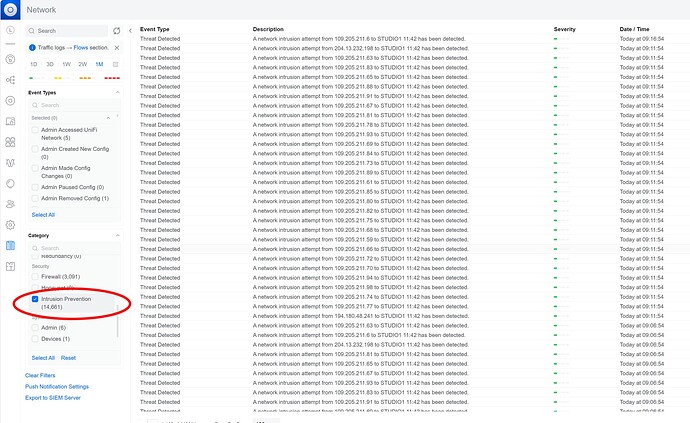
14,660-something attempts to gain access to the PC in my studio from some entity in Azerbaijan via using an old forwarded port I left open for Remote Desktop. With that many attempts, its a really good thing I have a strong password. Plugged that security hole just now!
Glad you don't have an alarm set for intrusions like me, that would blow up my phone, for sure LOL
Another reason to setup VPN and the firewall...
This was the old hole I left open as an alternate incase something happened to the VPN server. Ironically, the port forwarding rule for this was named "unsecure-bad idea"
I run a small business website on the public internet via a AWS EC2 instance.
I'm likely seeing 10K attacks, probes, vulnerability & port scans, etc per hour. - 60% of the monthly traffic are attacks, and 30% is either bots or AI spiders, and about 5%-10% is "real". Cloudflare rules and caching are effectively a requirement for any static public IP on the internet these days. - Even then, it's 100's of GB month of junk. The public internet is not a friendly place.
Not sure how this small site could stay up, without various security/CDN frontends. @bobbyD I'm sure the HE community website seems equal, if not more, attacks, probes, etc.

I used to see similar when I'd port forwarded for remote CCTV access. If the standard http and server ports were kept, the logs were full of 'illegal login' attempts, literally thousands over an hour or two. Using non standard ports helped but I wouldn't use port forwarding any more.
I thought I would be safe using a non-standard port. Rather than exposing the RDP port (3389) to the outside world, I used a random port (17273). Apparently that doesn't help though...
I install CCTV and up until about 8 years ago, Hikvision were recommending port forwarding as their own service was so woeful. It's all cloud p2p now and the service works very well. We are almost forced to use that cloud connection as all of the best features in the apps are unavailable without it, making VPN a non starter.
Unfortunately, it does not. I've been in IT professionally for over 30 years. Port forwarding, unless needed for a very specific use case, has gone the way of the Dodo Bird.

ya vpn server is now the way to go allow rdp access. even that has issues as people try to hack the vpn ports.. sigh
Since I’m not expecting any incoming connection attempts from about 99.999999% of the world, I use unifi’s geo-blocking feature to automatically drop unsolicited, incoming traffic from pretty much every country.
Smart!
Exactly what it is for!!
I’ve considered setting that up in my UniFi but am concerned I’d block required traffic. Guess I should start with China and. Russia
I block chins khazickstan Russia and brazil
I also block Antartica - just 'cause wha?
Since this blocks only those connection attempts that start from those countries, you’re probably pretty good to enable it very broadly.
Unless you’re hosting a service publicly and expecting people in a given country to connect to it.
It won’t prevent you or anyone else on the local network from initiating a connection to a server in the blocked countries.
The return traffic from that outgoing connection is generally allowed unless you create additional firewall rules manually.
ETA: I should clarify it’s possible to configure it for “both directions” or “outgoing.” If you wanted to prevent anyone on your network from reaching out to Russia or china, for example. But then you might end up blocking benign traffic like some IoT devices.
Personally, I’m most concerned about unsolicited connection attempts from outside, so I only block “incoming.”
thanks @marktheknife - I'll take a look and start locking things down.
to me its amazing how hard some of these spam sites hit you.. i have other blacklists in my firewall in additon to blocking those countries (both in and out).. basically anyone that sends spam to my email server or keeps trying to pentrate it i block them.. sometimes whole class c's if they keep rotating ips on their spamming servers..
my firewall loads the latest ip lists for those countries and i reload the entire firewall about once a week.. in the 20 odd seconds it is down while removing the old ip list (now about 40,000 entries) and refreshing i now get a few spam emails through on ips i already block!.. so they must be hitting the server continuously..