I've got three (assumed IoT) devices on my Wi-Fi network I'm trying to ID...any suggestions appreciated. Did some Googling but didn't find any helpful wisdom. Espressif is in Shanghai...

I've got three (assumed IoT) devices on my Wi-Fi network I'm trying to ID...any suggestions appreciated. Did some Googling but didn't find any helpful wisdom. Espressif is in Shanghai...

The numbers after "_" is a part of MAC Address (last 3 hex numbers, sometime in reverse). This may help. Otherwise ping each one and power off one by one.
Ws-gateway is your ecowitt hub.
Do the ESP boards usually have a web service on port 80? You could try just going to the IP in a web browser and see if anything comes up.
Expressif in my system according to my ip reservations are ecowitt and some kasa switches.
Also my konnected boards.
Thanks! One mystery solved!
Thanks, but I don't have any Kasa devices... I have some Tapo plugs but those were identified properly.
I had tried that but hadn't gotten any usable information out of a MAC address search.
Thanks, I'll try that next, good idea.
Unfortunately, hitting the IP addresses on port 80 didn't work, "refused to connect."
May end up doing that...
I've gone through my devices that use Wi-Fi, looking for the ones that aren't getting identified. I'll give that another run, must be staring me in the face and I'm not seeing it...
One is showing some activity, so something is happening... ![]()
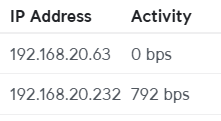
Two remaining mysteries. MAC addresses' three leading pairs only point to Espressif...
e8:db:84
dc:4f:22
Download advanced port scanner. It will tell you what ports are available and possibly identify the manufacturer.
Total long shot, but perhaps you can scroll through the tasmota supported devices list (templates.blakadder.com) to see if you own any of those devices. Many of those devices run esp boards. You should be able to filter by region.
My parents have a couple espressif devices on their dhcp lease list… they’re putting those boards in all sorts of things.
Do you have some "dongles" that connect some equipment to wifi? My solar inverters [EG4) show up as espressif on my wifi, via their dongles. Only way I found to identify which is which is unplug them one at a time.
good old nmap -sV [ip] (-p- if necessary) might provide clues.
Yeah I used nmap to ID a device once, I still have my script saved on my router. I used:
nmap -v -sS -sU -A [IP]
The -v gives you extra verbose output.
Any Lifx or Wiz bulbs?
Is "nmap" a Linux command (it looks like it does not exist on Windows)?
I have tons of Espressif devices. I know very well what they are but it will be nice if I can run this command somewhere. My router is ASUS RT-AX88U. Is it possible to run this command on the router?
EDIT
SSH is enabled:
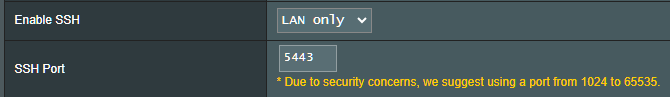
But I have no idea how to use it (i.e. how to connect to router using SSH from Windows PC).
I have a couple of Sengled WiFi Matter bulbs that ID as Espressif on my router.
Yes its Linux command and it can be run from the Asus router but you would need to have entware installed to install the nmap package.
Looks like there is a windows version you can download and it even comes with a GUI: Download the Free Nmap Security Scanner for Linux/Mac/Windows
Thanks...both come up like below, no new info:
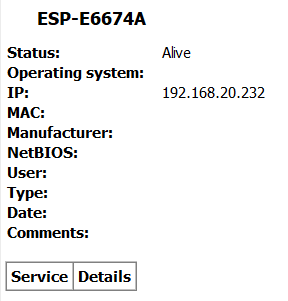
Thanks, but didn't see anything I have...I don't buy Wi-Fi stuff HA gear generally, never played w/Tasmota, and other than the Eufy vac entry (and my Eufy was properly found in the AP device list) didn't see anything that matched up w/my house. Thanks for the suggestion - freaking long list of products!! ![]()
I have a comm unit from Solar City for our solar, but that got properly identified. Thanks, good suggestion.
Nope, thanks for asking.
Tring the nmap...thanks for the suggestion.
Using: nmap -v -sS -sU -A 192.168.20.63
Seems not finding anything very useful, unfortunately:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-23 08:46 Pacific Standard Time
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 08:46
Completed NSE at 08:46, 0.00s elapsed
Initiating NSE at 08:46
Completed NSE at 08:46, 0.00s elapsed
Initiating NSE at 08:46
Completed NSE at 08:46, 0.00s elapsed
Initiating Ping Scan at 08:46
Scanning 192.168.20.63 [4 ports]
Completed Ping Scan at 08:46, 9.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:46
Completed Parallel DNS resolution of 1 host. at 08:46, 0.00s elapsed
Initiating SYN Stealth Scan at 08:46
Scanning ESP_08DA28 (192.168.20.63) [1000 ports]
Completed SYN Stealth Scan at 08:46, 1.22s elapsed (1000 total ports)
Initiating UDP Scan at 08:46
Scanning ESP_08DA28 (192.168.20.63) [1000 ports]
Completed UDP Scan at 08:46, 6.13s elapsed (1000 total ports)
Initiating Service scan at 08:46
Scanning 1 service on ESP_08DA28 (192.168.20.63)
Completed Service scan at 08:48, 102.64s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against ESP_08DA28 (192.168.20.63)
Initiating Traceroute at 08:48
Completed Traceroute at 08:48, 0.03s elapsed
Initiating Parallel DNS resolution of 1 host. at 08:48
Completed Parallel DNS resolution of 1 host. at 08:48, 0.00s elapsed
NSE: Script scanning 192.168.20.63.
Initiating NSE at 08:48
Completed NSE at 08:48, 14.03s elapsed
Initiating NSE at 08:48
Completed NSE at 08:48, 1.03s elapsed
Initiating NSE at 08:48
Completed NSE at 08:48, 0.00s elapsed
Nmap scan report for ESP_08DA28 (192.168.20.63)
Host is up (0.0088s latency).
Not shown: 1000 closed tcp ports (reset), 999 closed udp ports (port-unreach)
PORT STATE SERVICE VERSION
1900/udp open|filtered upnp
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized
Running: lwIP
OS CPE: cpe:/a:lwip_project:lwip
OS details: lwIP 1.4.0 or earlier, lwIP 1.4.1 - 2.0.3
Network Distance: 2 hops
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 6.00 ms unifi.localdomain (192.168.10.1)
2 6.00 ms ESP_08DA28 (192.168.20.63)
NSE: Script Post-scanning.
Initiating NSE at 08:48
Completed NSE at 08:48, 0.00s elapsed
Initiating NSE at 08:48
Completed NSE at 08:48, 0.00s elapsed
Initiating NSE at 08:48
Completed NSE at 08:48, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 138.38 seconds
Raw packets sent: 2289 (105.156KB) | Rcvd: 2154 (104.618KB)
Do you have a Broadlink device?
Block the ips in your router and see what stops working...
Also try a port scan on them to see what ports it answers to if any.
I don't, at least as far as I know. Nothing branded Broadlink. No standalone RF/WiFi/IR blasters.