Powerwall Manager version v0.3.30 is now available. This update includes the option to specify a refresh token instead of an access token, eliminating the need to enter a token every 45 days. The update also includes the ability to command and schedule off-grid operation. Both app and driver should be updated for this change. Thank you @x10send.
I've got the Tesla server logon working with the refresh token but am having trouble with the local access setup. From a browser I can log onto the gateway with the last 5 of the password on the gateway sticker. On the local access setup I'm getting a timeout error.
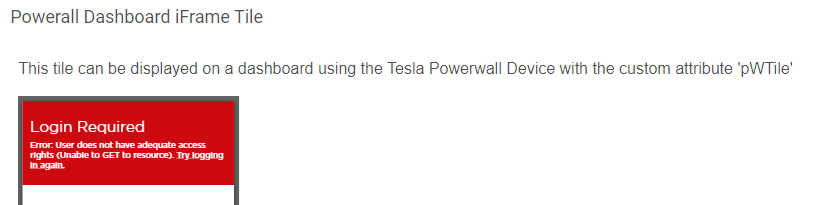
For the dashboard setup I get this error.
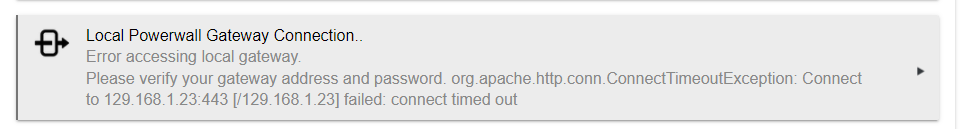
I am using the same IP and last 5 password that works from a browser and the Hubitat and gateway are on the same network. I also have the latest version of app and driver.
It's certainly possible that I'm not robustly handling this particular network configuration properly in the code, but the ConnectTimeoutException makes me wonder if maybe Hubitat can't reach the Powerwall Gateway's subnet. (Otherwise, if the subnet was valid to Hubitat, but the IP wasn't, it would likely result in a "no route to host/unreachable" error, and a simple password authorization error should give you a "401 unauthorized" error).
Do you have any other pinger or Powerwall apps or drivers installed on Hubitat that you can use to verify that your Hubitat can see the gateway's address?
As far as the Dashboard Tile iFrame issue, I'm now seeing this same dashboard error you have captured above when running on Chrome. Safari now also has a different problem, although Firefox and Fully Kiosk Browser both still seem to work for me when displaying this as a tile on a Dashboard. All my dashboards run on FullyKiosk, so I hadn't noticed any issues. I'm wondering if Chrome and Safari have added additional protection against iFrame access - or at least the way I'm implementing this. I'll investigate further. There may be a way to permit this for certain browsers.
@Darwin I'm using your app/driver pair. I find that it fails to automatically refresh the Powerwall values. It only updates if I manually click poll and refresh - but when I do, it successfully gets updated values. However, it never updates on the polling interval. I've updated to the latest (Jan 19) version and that hasn't made a difference.
I'm using the local gateway connection - no Tesla token is configured. I turned on debug logging and I see this in the logs:
[debug] Input Access Token Valid: false
and looking at the code, that looks like a path to validate the Tesla token (which I said is not configured in the app).
I'm using Snell's driver pair, also, and it doesn't have an issue talking to the local gateway connection. But I like the notifications in your app better.
Any ideas on how I can debug this?
.
UPDATE: I uninstalled and re-installed the app and reinitialized it. It did one query, then it logged this on the time for the 2nd query:
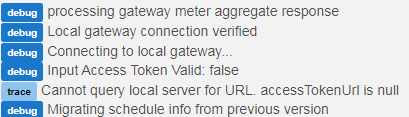
but it proceeded to query the device, so at the moment it is working.
I typically run with both server and gateway polling enabled and admittedly don't do too much testing with just the gateway. I was going to suggest re-entering the gateway data to re-initialize the polling, but your clean install certainly takes care of that. It's very possible I failed to migrate one of the updates properly and your set up needed a full-initialization to get things properly working again. Let me know if this rears its ugly head again. I'll toss in a few more debug or trace statements in this area for future reference.
The network is all on 192.168.1.x. I don't have any other apps on the Hubitat connecting to the gateway, but the Hubitat does connect via IP to some Lifx bulbs and the Envoy gateway for the solar panels. I can't think of anything network wise that would get in the way. The Powerwall gateway is hardwired to the router.
This is a new Powerwall. Is there anything that should be done on its setup? I have not logged in as installer yet to check what the contractors set up in there.
I don't use this app (I use Node-RED to access my Powerwall) but I have possibly been having a similar issue with my Powerwall+ (installed late December). I cannot reach (either through a browser or ping) the Powerwall+ from any of my local machines EXCEPT one RPi that is connected directly to my router. I haven't been able to figure out what the root cause is, but since my Node-RED is running on that RPi, I can at least grab the data.
Have you tried configuring the wifi on the Powerwall to connect to your router and seeing if that works?
Yes, on the off chance it might work I did set up the WiFi connection on the gateway, confirmed it worked by accessing the IP on a PC browser, then tried that IP instead of the wired one in the local setup for the app. Same error.
I added a gateway ping test option on the Powerwall Manager app local gateway account page and also added some additional Hubitat Log debug and trace statements (general preferences page to enable) on the pre-release line here. It doesn't fix anything yet, but maybe it can help narrow down issues.
This is what I get on the Ping and below that the logs with it set to Trace. It just looks like the gateway is not responding to it. Still can't think of anything network wise that would block it. Do you think the user not authorized for GET error on the dashboard setup has anything to do with it?
09:55:49 [rttAvg:0.0, rttMin:0.0, rttMax:0.0, packetLoss:100, packetsReceived:0, packetsTransmitted:3]
TRACE
search
app:4962022-01-29 09:59:23.627 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:59:13.590 am tracePosting to gateway URI: https://129.168.1.23/api/login/Basic
app:4962022-01-29 09:59:13.588 am debugConnecting to local gateway...
app:4962022-01-29 09:59:05.676 am debugbattery found: STE20220124-00121 site_name: Nicholls&Fenton energy_site_id: 283389897812
app:4962022-01-29 09:59:05.094 am debugInput Access Token Valid: true
app:4962022-01-29 09:57:11.115 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:57:01.092 am debugConnecting to local gateway...
app:4962022-01-29 09:56:48.742 am debugprocessing server site data response
app:4962022-01-29 09:56:39.785 am debugprocessing server powerwall response
app:4962022-01-29 09:55:49.396 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:55:39.377 am debugConnecting to local gateway...
app:4962022-01-29 09:55:39.293 am debugGateway ping results: PingData(rttAvg: 0.0, rttMin: 0.0, rttMax: 0.0, packetsTransmitted: 3, packetsReceived: 0, packetLoss: 100)
app:4962022-01-29 09:53:47.241 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:53:37.218 am debugConnecting to local gateway...
app:4962022-01-29 09:50:28.177 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:49:35.549 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:49:08.465 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
app:4962022-01-29 09:47:11.159 am warnError getting local gateway status: org.apache.http.conn.ConnectTimeoutException: Connect to 129.168.1.23:443 [/129.168.1.23] failed: connect timed out
The user not authorized issue on the dashboard I believe is an unrelated problem with some browsers with enhanced security not wanting to handle the gateway login via an iFrame. This happens with Chrome and Safari on my system as well. The fact that this page shows at all is a good sign that your computer can see the gateway OK.
On the Hubitat->Settings->Network Setup->Network Test page, do the gateway pings and trace route tests look OK? I can't imagine issues there though, or you would likely be seeing other issues besides this app, but I thought I'd ask.
At least your outside Tesla server connection appears to be working, but I'm at a loss for what else to try aside from re-booting Hubitat and/or your network equipment. But that would make me sound like a Cox support tech. You could try reconnecting your Powerwall networks and renewing leases by logging into the gateway webpage as customer and clicking on "Connect" on the Network->Ethernet page - or try a Static IP on that page vs DHCP. Or try re-selecting your wireless network on the gateway Wi-Fi page to renew that lease..
Well it ended up being a stupid reason for the local not connecting. If you notice in the log I had 129 instead of 192 in the IP. Came down to a typo. Works now that I have the correct IP.
Dashboard still has the get error, but that's a different thing. Had the IP correct on that screen which is why that did no time out.
I didn't notice that either. Glad it's working now.
Powerwall Manager v0.3.60 is now available and includes the following changes since the v03.30 post:
v0.3.60: Added Storm Watch Active status, added delta Watt threshold preference setting for power reporting, enabled dimmer level for reserve control/status using the base Powerwall device, added child device creation options for some states and power meter values.
v0.3.50: Fixed issue with delta check update logic resulting in power level updates not always being sent as expected.
v0.3.40: Added option to choose between multiple Powerwall sites when available. Fixed issue with actions and alerts when returning to on-grid.
Both app and device driver are required to be updated with this change. The Powerwall Manager is also now available in Hubitat Package Manager.
@Darwin - Is this app still working with recent API updates from Tesla, or is this still local-only? We’re working on @kahn-hubitat’s Tesla car integration to try to update the app due to the recent changes. Many of us were manually updating the token which only refreshed every 45 days, but now with an 8-hour refresh it’s unmanageable. So it was suggested we might be able to use what you did with Powerwall in this app. Any help would be appreciated!
Yes, the Powerwall Manager is still working with Tesla's recent API updates. The method to refresh the tokens is void refreshAccessToken() on line 620. It will schedule this as needed based on the expiration date of the last token received. There's a second try/catch in this method that attempts to get the old 45 day access tokens from bearer refresh token just in cases that starts working again. This second try/catch always fails after Tesla's latest changes, so you can probably leave off that part.
I can possibly look at adding this code in to Tesla Connect app if no one else gets to it, but probably wouldn't be able to look at it for a couple of weeks. I currently don't have my 3 integrated in, but it's probably about time. For those that use both Tesla Connect and the Powerwall Manager, it would be nice to have the option to have just one app keep both tokens updated.
I also saw that the option to not follow HTTP redirects was added in the Oct 2.29 Hubitat update, so it may actually be possible to once again use username and passwords in Hubitat with Tesla's latest auth updates. I haven't looked at that yet to verify.
Thanks so much for this info!!
I’ll take a look at it and see what I can do in the meantime, although probably above my skill level. Kahn and others are in the loop too, so hopefully we can get it done.
Yeah, totally recommend it. I use Tesla Connect to run all my voice controls (iOS and Alexa), set charge levels based on calendar events and location, perform location-based triggers, etc.
Had my first nighttime power outage with the Powerwalls. It unintentionally set off the intrusion alarm with this app. I had the trigger for nightime intrusion set to all contact sensors. I did not realize the Powerwall device appeared as a contact sensor and when it went off grid it triggered the intrusion alarm. I've now set the intrusion alarm to manual sensor selection and left the Powerwall device out of its triggers.
Sorry about that! Yes, the contact sensor capability to indicate power outage was added a while back from an enhancement request as a simple way to trigger power outage voice notification on echo devices. The description for the contact sensor capability is buried down in the general preferences section, but it may worth making that a little more obvious.