Continuing the discussion from [UPDATED] iPhone WiFi Presence Sensor:
I think that here is a good place for it.
As we know, it's a good "practice" to put IOT devices on a separate subnet, for reasons of security. Furthermore, as we see from many commercial installations (some of which I have done myself), CCTV cameras are often put on their own, with a separate NVR, on their own subnet.
So, I thought to myself, why not put CCTV cameras on their own Router and network? Especially since the routing demands are expected to be significant.
So, my next thought was , "why not put my Hubitat hubs on that same router/network, for security reasons?"
However, the issue became "how do I route between networks?" This is important for things like presence, homebridge, maker api, etc.
I couldn't think of any way to do that (in my knowledge of networking), and that's why I posed the question.
I can always put JUST my CCTV cameras on that separate network, if I can't resolve this routing issue.
That makes sense. I agree it is a good practice. The way I have done it is they are all on one network but segmented into VLANs, each VLAN containing a single subnet. One VLAN for IoT, one for guests, one for home automation, one for gaming devices, one for end users, and one for management. I use a firewall to block access from one VLAN to the others, but open up some devices so they can talk across VLANs. Then I take some of the VLANs and map them to access points and SSIDs. So a user device can either plug into a switch or connect to an access point, but the management network and home automation network are only hard wired. Then use firewall rules to allow end user devices to get to the hubs on the home automation network.
If you put your CCTV cameras on their own network, any device that you want to access the cctv cameras directly (or access the network dvr) will also have to be on that same network. Or you'd have to somehow connect that network to the internet and make the nvr available that way. However, if you put them on their own VLAN, you can create firewall rules to allow certain traffic back and forth between the two VLANs.
The only compunction that I have with using one network, is the "resource consumption" issue. As mentioned previously, those 4K streams are very large, and attaching an "always on" NAS to allow them to write to it, is going to be a significant resource issue, no matter what type of networking gear I use. That's why the answer came up "use a separate router for that.
I think we may mean two different things by "one network." With the right network equiment and configuration you can segment camera traffic and keep it all local to the same VLAN and even network switch. There are also network switches that support PoE and have NVRs built into them - Unifi makes a nice one. But... none of this is readily doable with the gear you have now.
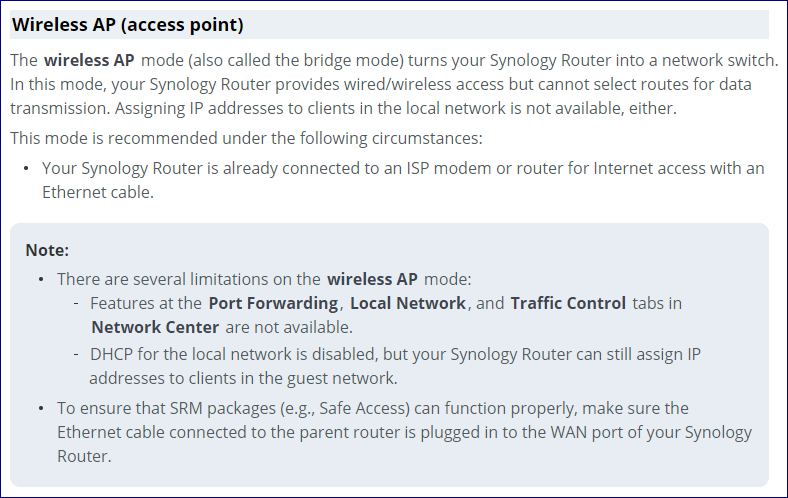
You might be able to use one of your routers in bridge mode (turn off NAT) and kind of accomplish what you want to do as long as you could fit your network DVR and your cameras all on whatever switch is built into the router and as long as the switch really did act like a switch, so to speak. This would not resolve your security concerns but might keep most of the camera traffic local. But you're much better off going with more commercial-grade gear and doing it right from the ground up. I assume your cameras are all hard wired... maybe not a valid assumption?
Hard-wired?
The last job that I did, I was called in when there were no walls and no ceilings, so I was able to run cat6 poe cables through out. (I also put in a UBiquiti UDM Dream PRO).
However, unfortunately, now we are talking about wireless cameras, sending 4K streams via wifi, and a number of them. That's why I have a resource issue.
Ugh. What about taking one of your routers, sticking it in bridge mode, plugging it into the first router, and just using a separate SSID? If you hang the NVR off the switch on that router the camera traffic should all stay local to that wifi network and switch. Not going to address security at all but might help performance, and it doesn't matter where you put the hubs.
Precisely.
I assume that if I switched to this mode:
- all the traffic from the cameras would all be handled by this router (that would handle the resource issue).
- DHCP would be the responsibility of the "other" router - this would allow me to put all the CCTV stuff on a separate vlan. (e.g. 192.168.10.X)
- I would use subnet routing to go from one subnet to another.
Not quite. When you go into bridge mode you basically shut down all routing on that device. And you would have a single subnet across both devices.
#2 would be true for DHCP but there are no VLANs in this scenario.
VLANs and subnetting are outside my comfort zone, so maybe this question is way off base.
But if you have two separate routers, as opposed to one router with multiple VLANs, how do you route between the two?
You don't.
That’s what I thought.
Is that what OP is intending to do?
I think he's got two desires. One is to separate the camera traffic and keep it as local as possible to the NVR so it's not flooding his network. The 2nd is security, which is not really achievable in this model.
That's what I was asking how to do, because I couldn't figure it out.
Turns out it's not really possible.
Well I say "you don't" kind of quickly. I suppose you COULD connect them together and allow both to function as routers and do what's known as "double NATting." But it isn't what I would consider "best practice." It might be worth giving it a try though. It creates interesting issues when routing from one to the other - I've honestly not had much experience with it but you could try it.
Since DHCP is the responsibility of the "other" router, couldn't I reserve some DHCP addresses on it as "192.168.10.X" for the camera stuff, and "192.168.1.X" for everything else?
On something like a UDM, yes absolutely. On your devices, I doubt it. How about just tossing out the existing gear and putting in a nice Unifi network?
Either to install some ubiquiti networking gear, or to give up on the security issue... Hmm... we'll have to see.
However, if I do the "bridge" mode approach, at least I will have dealt with the "resource" issue, in that all traffic associated with the cameras will go through the Synology router.