Are you using any "content" filtering on your firewall, or using something like PiHole?
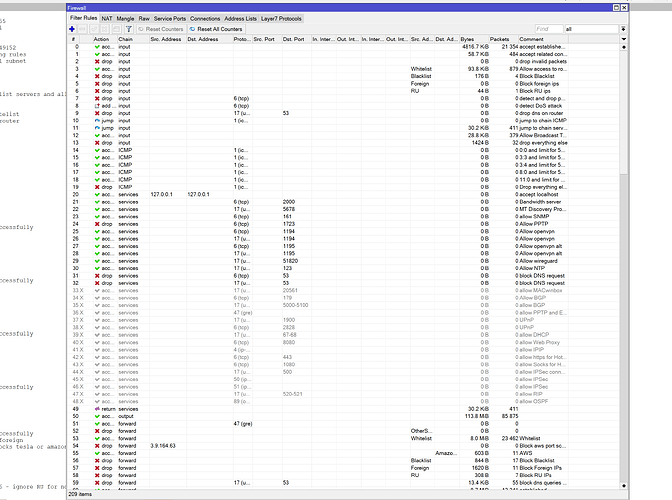
iptables. as the rules above show. no content just protocol, interface, port, source and dest filtering..
as well as special rules for state ie established and frequency
ie examples
and downloaed/updatedable address lists for instance to block all of china, russia etc.
/put "normal output and forward rules start here"
add chain=output action=accept
/put "allow gre open for vpn"
#add chain=forward action=accept protocol=tcp dst-port=1723
add chain=forward action=accept protocol=gre
/put "block other ips on our subnet"
add chain=forward action=drop src-address-list=OtherSubnetIPs
/put "our trusted subnets"
add chain=forward action=accept src-address-list=Whitelist comment="Whitelist"
add chain=forward action=accept dst-address-list=AmazonAWS comment="AWS"
/put "Blacklist"
add chain=forward action=drop src-address-list=Blacklist comment="Block Blacklist"
/put "Foreign"
add chain=forward action=drop src-address-list=Foreign comment="Block Foreign IPs"
/put "Foreign RU"
add chain=forward action=drop src-address-list=RU comment="Block RU IPs"
/put "also block dns queries more than 2/5 secs"
add chain=forward protocol=udp dst-port=53 action=drop limit=2,5:packet comment="block dns queries no more than 2 /secs"
/put "established connection rule"
add chain=forward action=accept connection-state=established comment="established"
add chain=forward action=accept connection-state=related comment="related"
example of specific port(s) rule
/put "allow wireguard from whitelist and allowed imapips and comcast"
add chain=forward action=accept protocol=udp src-address-list=Whitelist dst-address=173.14.182.124/32 dst-port=51820 comment="allow wireguard"
add chain=forward action=accept protocol=udp src-address-list=AllowedIMAPIPs dst-address=173.14.182.124/32 dst-port=51820 comment="allow wireguard"
add chain=forward action=accept protocol=udp src-address-list=ComcastPublic dst-address=173.14.182.124/32 dst-port=51820 comment="allow wireguard"
another
/put "allow time setting udp only"
add chain=forward action=accept protocol=udp dst-address=173.14.182.0/24 src-port=123
and on and on and end of firewall
/put "disallowing syn floods"
add chain=forward protocol=tcp tcp-flags=syn connection-state=new action=jump jump-target=SYN-Protect comment="SYN Flood protect" disabled=yes
add chain=SYN-Protect protocol=tcp tcp-flags=syn limit=400,5:packet connection-state=new action=accept comment="" disabled=no
add chain=SYN-Protect protocol=tcp tcp-flags=syn connection-state=new action=drop comment="" disabled=no
# drop all else
add action=drop chain=forward comment="drop all else"
/put "get Foreign lists"
/put "get china list"
/tool fetch url=http://www.iwik.org/ipcountry/mikrotik/CN
/import file-name=CN
/put "get russia list"
/tool fetch url=http://www.iwik.org/ipcountry/mikrotik/RU
/import file-name=RU
/put "get kz list"
/tool fetch url=http://www.iwik.org/ipcountry/mikrotik/KZ
/import file-name=KZ
/put "get br list"
/tool fetch url=http://www.iwik.org/ipcountry/mikrotik/BR
/import file-name=BR
/put "combine lists for those we block"
/put "combining CN"
/ip firewall address-list
set list=Foreign [find list=CN]
/put "combining KZ"
/ip firewall address-list
set list=Foreign [find list=KZ]
/put "combining BR"
/ip firewall address-list
set list=Foreign [find list=BR]
/put "combining RU"
/ip firewall address-list
set list=Foreign [find list=RU]
} on-error={ /put "error occured... loading emerg firewall"
/import firewall4emergency }
its actually more complicated than some as my ip subnet is on the same subjet as my gateway (and to route they need to be on different subnets) so the firewall is actually a bridging firewall that bridges between my gateway and my subnet block.
between 2 ports on the router.
unfort. that is the way comcast gives out static ip blocks..
Assuming this is a Linux variant, can you use tcpdump with the device running the app as the host?
See what is sent and dropped.
they dont have tcpdump but they do have a packet sniffer any maybe i can sniff what is dropped on to my phone.. thanks again for inducing me to look.
ie
i think i checked it out before though and it is not in conjuction with the firewall so doesnt show me packets that are dropped and the amount of data is just huge..
i can log packets before dropping them but i am not sure which rule is causing the app not to run.. unfortunately and there are too many packets being dropped to filter all of them..
maybe i can add a new rule before the drop all else to drop specifically for just the one public to private ip router and see if that rule is doing it.. but i have a feeling it may be something else like they are using some random ip that is in my blacklist or foreign ip block list..
ie
'
You definately are not using any Dnsbl or ad blocking services?
no i have my own coded blacklist that is compiled from looking at my nightly email report for ips and subnets of ips that are trying to hack my email server (ie thousands of failed login attempts)
the problem could be something there as i am sometimes overzelous.. ie if i get hundreds of hacking attempts from and ip and then maybe 2 or 3 more in the same class c after i block it.. i will sometimes just write one rule to block the entire class c
ie
add address=209.182.100.0/24 disabled=no list=Blacklist
add address=209.182.102.0/24 disabled=no list=Blacklist
add address=209.182.103.0/24 disabled=no list=Blacklist
but in the past i have gone through and disabled the blacklist blocking rule to test it and for instance the app i am looking at still would not work...
and also as i said and is above a list of all russia khazekstan, brazil etc ip blocks as the majority of hacking attempts come from them..
i do have active spam for email outside of the firewall.. that is built in to the email server (goes out and checks its own blacklists) before allowing the email through... but that has nothing to do and is outside the perview of the firewall.
i also think the problem could be some dns server lookup issue getting blocked as sometimes the app will not run on the phone, so i disable wifi .. run the app.. and then when wifi is back on it works for awhile..
You may or may not be your own worse enemy. ![]()
This might be a new thread discussion, maybe in the lounge. ![]()
Maybe a discussion about what people are using for their firewalls, rules and pros/cons of each.
Could be an interesting discussion.
You really think there are enough people on here either with public ip blocks and custom firewall or not just using the out of thr box nat forwarding firewall maybe eith one or two ports opened up?
Maybe i know from reading the threads there are plenty with screwed up networks configs with multiple dhcp servers and/or doube nat. ![]()
Did you authorize any 3rd party OAuth solutions?
For example if you authorize SmartThings via HubiThings Replica it establishes a webhook with the hub external URL that allows for two way communication. Anything like SharpTools, Ecobee, would do the same. Normally they need a stay alive before they stop.
You never know.
You definitely have too much free time.
Not that onerous. Maybe one or two ips a week . And i do.it once at end.of week.
This topic was automatically closed 365 days after the last reply. New replies are no longer allowed.