Hi,
Just got a Hubitat hub. Haven't had time to add any devices except ipad running hubitat app.
Problems: Thousands of DNS queries from hub to my PiHole DNS server.
Details
Hub Details
Hubitat Elevation™ Platform Version
2.1.0.123
Hardware Version
Rev C-5
Hub UID
IP Address
192.168.1.81 of Hub
PiHole
Recent Queries (showing queries for client 192.168.1.81)
Search:
Show entries
Previous12345…1077Next
Time Type Domain Client Status Reply Action
Time Type Domain Client Status Reply Action
2019-05-31
07:06:19 PTR 200.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.3ms) Blacklist
2019-05-31
07:06:19 PTR 200.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.9ms) Blacklist
2019-05-31
07:06:19 PTR 200.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.4ms) Blacklist
2019-05-31
07:06:19 PTR 200.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.3ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.5ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.3ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (10.3ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.7ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.5ms) Blacklist
2019-05-31
07:06:18 PTR 1.1.168.192.in-addr.arpa 192.168.1.81 OK
(cached) NXDOMAIN (9.3ms) Blacklist
Showing 1 to 10 of 10,762 entries
Any suggestions?
Thanks,
1 Like
Is it the same as this issue? Request: Provide option to specify NTP Server to use, stop hard-wiring it to pool.ntp.org
If so, the more of us that contact support@hubitat.com the higher the chance is that this becomes prioritized for a fix.
I am seeing the same thing on my C4 version hub.
For a hub that is suppose to be local.. this seems a bit excessive.
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:50 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:50 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:50 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:50 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:50 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:50 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
May 31 06:47:51 dnsmasq[6560]: config 192.168.1.1 is NXDOMAIN
May 31 06:47:51 dnsmasq[6560]: query[PTR] 1.1.168.192.in-addr.arpa from 192.168.1.199
Hi
Seems to be trying to look up non-route-able reserved ip addresses.
Whatever the cause, this is bad/rude network behavior.
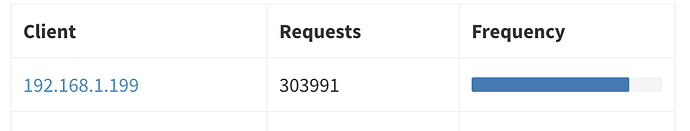
I am seeing over 10,000 requests in a 24 hour period from my hubitat.
To me, this is a critical error; a hubitat hub could take-down/make unusable a network it attaches to with all these requests.
Bad first impression for me with my new hubitat.
This is happening on both of my Hubitat hub. The second one does not have any app or device loaded yet. Just running the latest firmware. So this is not some user app doing.
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:18 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:18 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:19 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:19 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:19 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:19 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.208
Jun 1 09:23:19 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:19 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Jun 1 09:23:19 dnsmasq[6560]: config 192.168.1.25 is NXDOMAIN
Jun 1 09:23:19 dnsmasq[6560]: query[PTR] 25.1.168.192.in-addr.arpa from 192.168.1.199
Just started happening to me today on my Hubitat hub.
The only thing I did note is that Hue auto-updated its hub software at some time today as well. May or may not be releated.
The queries are all reverse-DNS PTR lookups for local IP addresses, apparently all devices that are registered in UPNP on my router. Started seemingly out of the blue, hammering my (local) DNS servers with approximately 2 PTR queries per second.
I removed my Hue-Hubitat linkage, nothing changed. I haven't removed SONOS yet. All the requests appear to be for things like my Samsung cameras, and the routers' address itself.
Are we missing a few zeros? 2p/s wasn't "hammering" 30 years ago back when CPUs and networks were both much slower.
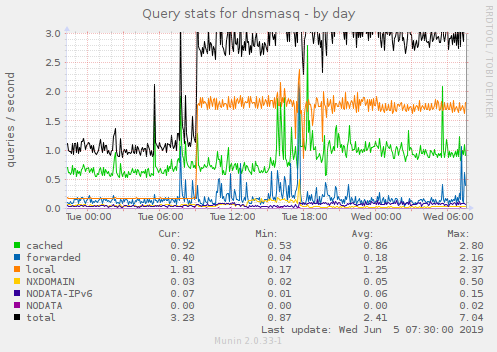
The logs above show 20+ queries per second which won't hurt the node, but certainly doesn't make a lot of sense.
Well, yes are correct - it's no big deal, except that it is 10-20x more than normal:
Which platform version is this?, and when was that version updated on this hub?
Hubitat Elevation™ Platform Version: 2.1.0.123
This version was installed on May 26:
systemStart System startup with build: 2.1.0.123 2.1.0.123 2019-05-26 11:18:35.727 AM EDT
The DNS "flood" started after I rebooted yesterday morning:
|systemStart|System startup with build: 2.1.0.123|2.1.0.123||2019-06-04 09:04:28.487 AM EDT|
And now, it mysteriously stops, almost exactly 24 hours later???
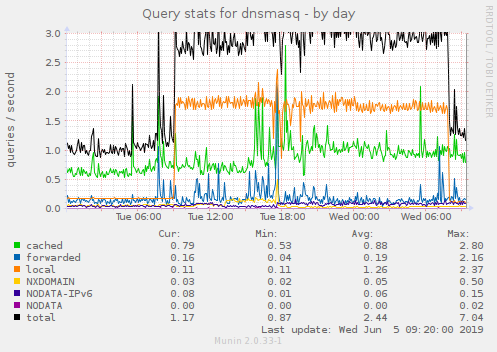
FWIW, the dnsmasq log shows that the hub started all this yesterday at 9:04:07am, 3 minutes after it had renewed its DHCP lease.
It stopped this morning at 07:52:57 immediately after the hub had refreshed its DHCP lease, and about 12 hours after the last time I rebooted the hub.
I rebooted the hub numerous times between these two events, and the DNS PTR lookups started back up each time after the hub restarted.
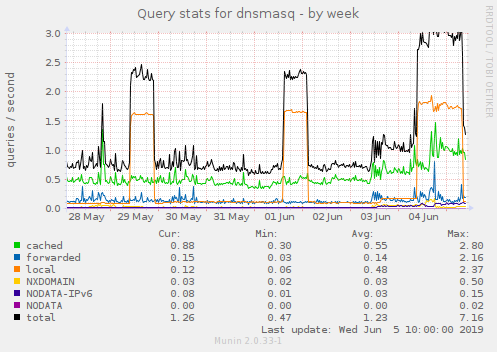
Looking back at the logs, it appears that this spike in DNS requests has been occurring about every 3 days, but only running for about 12 hours...(perhaps because I didn't reboot the hub on the prior occurrences).
It would thus seem that there is some specific logic that turns this behavior on and off for some reason...
1 Like
OK, we're looking into this as we speak...
We've tracked it down now, working on a fix.
9 Likes
This is resolved in 2.1.1, which is out now.
4 Likes
You guys have been busy. Kudos.
Its back even after cold boot
Hubitat Elevation® Platform Version
2.1.5.120
Hardware Version
Rev C-5
Hub UID
xxxx
IP Address
192.168.1.197
pihole
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.6ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.9ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.6ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.6ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.8ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.6ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.8ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.5ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.197 OK
(cached) NXDOMAIN (7.9ms) Blacklist
2019-09-28
10:40:11 PTR 7.1.168.192.in-addr.arpa 192.168.1.1